272 - final
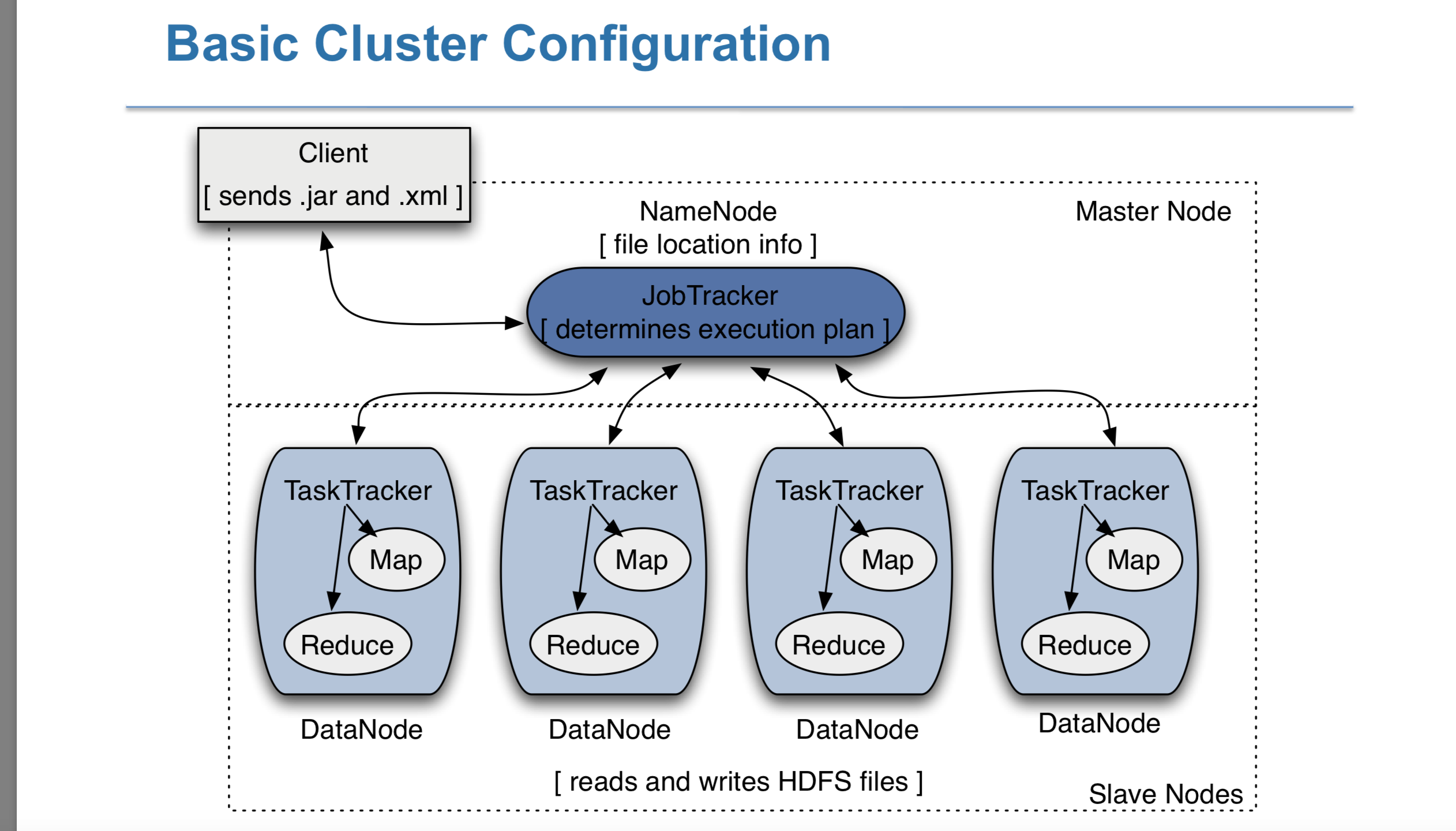
hadoop的cluster的configuration的图
dual gateway和single gateway的区别
persistent http和pipeline http的区别
The "persistent HTTP" approach can re-use the same TCP connection for Multiple HTTP transfers, one after another, serially. Amortizes TCP overhead, but maintains TCP state longer at server.
The "pipelining" feature in HTTP/1.1 allows requests to be issued asynchronously on a persistent connection. Requests must be processed in proper order. Can do clever packaging.
判断:
sql判断题 sql support a limited number of different formats for internal storage of information.?(F)
关于hadoop write once的 题目是write randomly (F)
Files in HDFS are ‘write once’ –No random writes to files are allowed
rts-cts collision的解决方法
curl的代码题
hadoop的map reduce的伪代码
关于3tier的开放式的设计题
Presentation tier: provide user interface, user can use this tier to operate the system.
Business logical Tier: supporting structure and business logic, receive the data from the presentation tier and send these data to data tier. Also, it will receive the data from data tier and transfer to Presentation Tier
Data Tier: access to database , receive data form Business logical Tier and return data to Business logical Tier from database.
Describe five step for X.509 public key certificate
- Generate private and public keys
- Gather name value pairs
- Generate Certificate Signing Request
- Submit Certificate Signing Request for CA to sign
- Receive certificate from CA
What does Trust mean?
“A” trusts “B” when “A” assumes that “B” will behave exactly as “A” expects
Web Trust Mode Disadvantages:
- Identify Spoofing with “bad” CA cert
- Decentralized Trust Management – user level management
- Inability for Revocation
- Distribution Problem – Who get what version of browsers?
1. sell computer web, architecture and technology
I will divide the website into three tier:
Presentation tier: provide user interface,
In this tier , webpages are directly processing all the operation from user, and show the info from business logical tier, like when user searching for a certain product, this tier will transfer the product name to next tier, after receiving the data, it will shows the product info to user. I choose html and css to construct UI interface.
Business logical Tier: supporting structure and business logic, receive the data from the presentation tier and send these data to data tier. Also, it will receive the data from data tier and transfer to Presentation Tier. In this tier, it will process these commands and do some logical decisions. For example, when user wants to view the top rated products in this website, Business logical Tier will receive all the data from data tier, and it will sort the results and transfer the top 5 products to presentation lier.
Data Tier: access to database, send the SQL query or insert command request to database, receive data form Business logical Tier and return data to Business logical Tier from database.
Database: The database contains several tables to save the information of customers or products, like the details info of customers, product info, transaction info and warehouse info. With this database, we can show the detail product info and price when user enter the product page. Every transaction will connect to database in order to trace the stock of products.
The method I would choose to transfer data in these 3 tiers is using REST API to connect, each tier can send HTTP request and receive response from the previous/next tier.
2. a. HTTP pipline b. 對於http standard 的enhancement 你可以做出什麼貢獻
a.
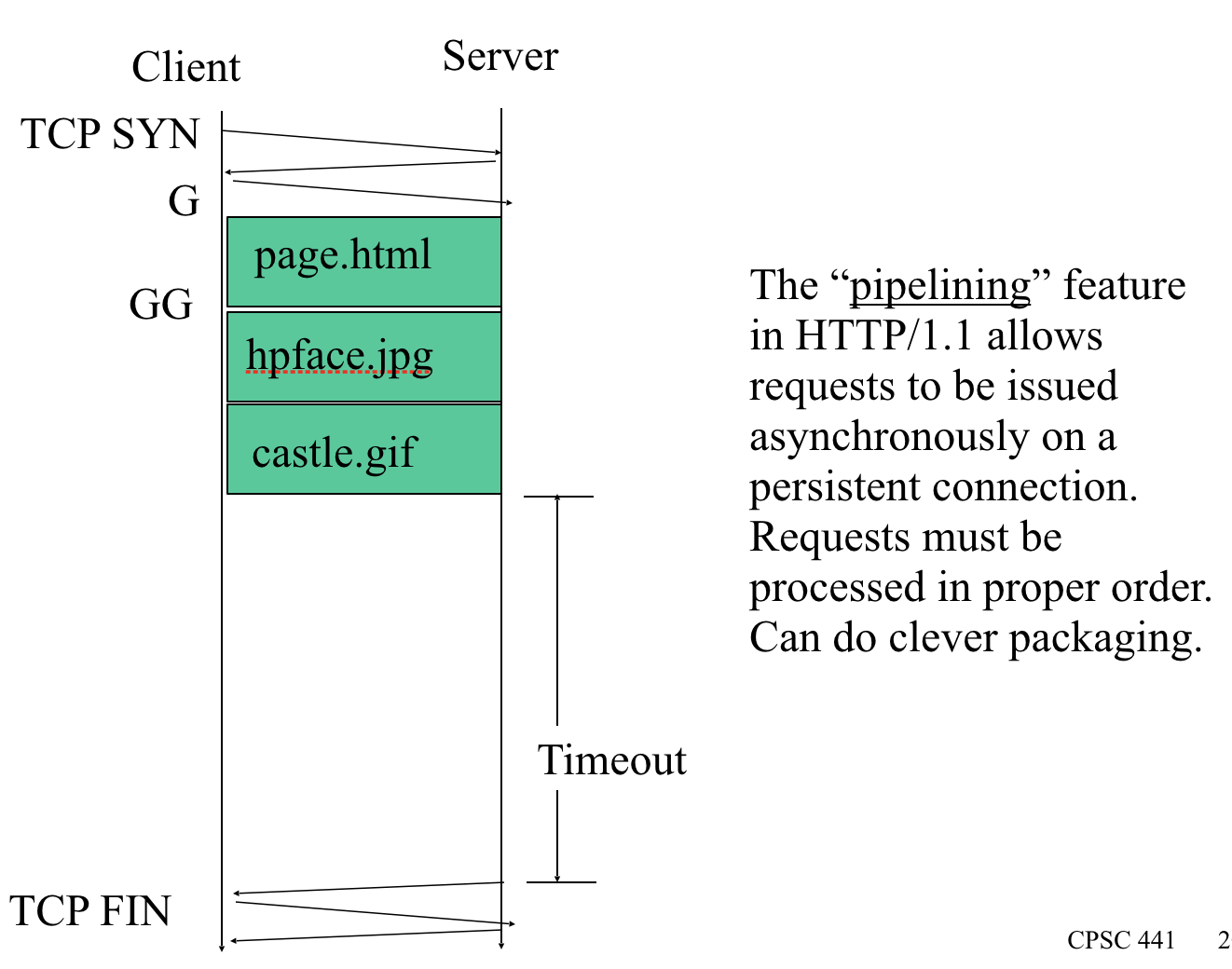
b. Http is based on TCP connection, every time the clients wants to get a data resource, it will send a TCP request for retrieving ACK response. After 3-Way Handshaking, server will start to send the data resource. However, the tcp connection will close the connection after finishing sending the data. If user needs to retrieve lots of data, it will generate lots of TCP connections and it cost lots of time on 3-Way Handshaking. Maybe we can develop some useful way to solve these problem, like transfer several data with different connections by reusing the same TCP connection. Or we can compress the http header to reduce the total amount of data.
3. curl download
$ch = curl_init(www.yahoo.com); / curl_setopt($ch, CURLOPT_URL, ‘http://news.google.com’;
$fp = fopen("myyahoo_homepage.txt", "w");
curl_setopt($ch, CURLOPT_FILE, $fp);
curl_exec($ch);
curl_close($ch);
4. RFID classic tag
- Passive -- energy from reader
- Active -- battery
- Semi-passive -- battery and energy from reader
5. HDFS reliability and availability
Data is replicated multiple times on the system for increased availability and reliability. Replicas are stored on different nodes
Therefore, if a node is failed, we still can retrieve data from the other replicas. It can improve reliability. Since there are some Replicas in different nodes. Although there is a busy or failed node, or there are lots of request to access one hot data, It will maintain its availability by serving the request with different other nodes. So, it can improve availability.
6. Reducer method code
reduce(output_key, intermediate_vals)
set count = 0
foreach v in intermediate_vals
count + =v
emit(output_key, count)
7. Geolocation
<script>
var x = document.getElementById("demo");
function getLocation() {
if (navigator.geolocation) {
navigator.geolocation.getCurrentPosition(showPosition);
} else {
x.innerHTML = "Geolocation is not supported by this browser.";
}
}
function showPosition(position) {
x.innerHTML = "Latitude: " + position.coords.latitude +
"<br>Longitude: " + position.coords.longitude;
}
</script>
8. Message 驗證
Message Authentication Code
Use secret key to address spoof data + hash problem
Use a algorithm to crate public/ private key, like RSA, User can sign a message with the private key, and anyone who has the public key can verify the signed message.
- Generate private and public keys
- Gather name value pairs
- Generate Certificate Signing Request
- Submit Certificate Signing Request for CA to sign
- Receive certificate from CA