272 - Enterprise Software Platform
RFID Technical Tutorial
RFID Stands for Radio Frequency Identification, and use radio waves to identification, which Provides unique identification or serial number of an object
RFID Reader is an **interrogator, reader powers passive tags with RF (Radio frequency) energy, so it consists of transceiver, antenna, micro processor and network interface.
RFID Tag is a device used to transmit information such as a serial number to the reader in a contact less manner, which can be classified by 1. Passive -- energy from reader 2. Active -- battery 3. Semi-passive -- battery and energy from reader
middleware, database
VeriChip: RF can penetrate mud, blood, and water, and the size is a uncooked grain of rice.
Supply Chain Management : adds visibility as the items flow through the supply chain from the manufacturer, shippers, distributors, and retailers.The added visibility can identify bottlenecks and save money. It also can reduce out of stocks.
EPC vs. UPC (Barcodes)
Same: Both are forms of Automatic identification technologies
Difference: 1. UPC require line of sight and manual scanning whereas EPC do not 2. UPC require optical reader to read whereas EPC reader reads via radio waves 3. EPC tags possess a memory and can be written while UPC do not 4. EPC tags cost 5 cents, UPC tags cost 1/10 cent
Hadoop
Open source, and it is developed from Cloudera which is the commercial Hadoop company
Traditionally, computation has been processor-bound. So, Distributed system evolved to allow developers to use multiple machines for a single job. However, Programming for traditional distributed systems is complex, like data synchronization, finite bandwidth, temporal dependencies.
Typically, data for a distributed system is stored on a SAN (Storage Area Network), but Getting the data to the processors becomes the bottleneck.
Therefore, they have to develop a new approach to meet the following requirements:
- Partial Failure Support : graceful degradation
- Data Recoverability: Failure should not result in the loss of any data
- Component Recovery : recover and rejoin
- Consistency: failures should not effect the outcome
- Scalability: allows adding loading and increasing resources
Hadoop core concept : distribute the data as it is initially stored in the system, Applications are written in high-level code
, Nodes talk to each other as little as possible, Data is spread among machines in advance(Replication)
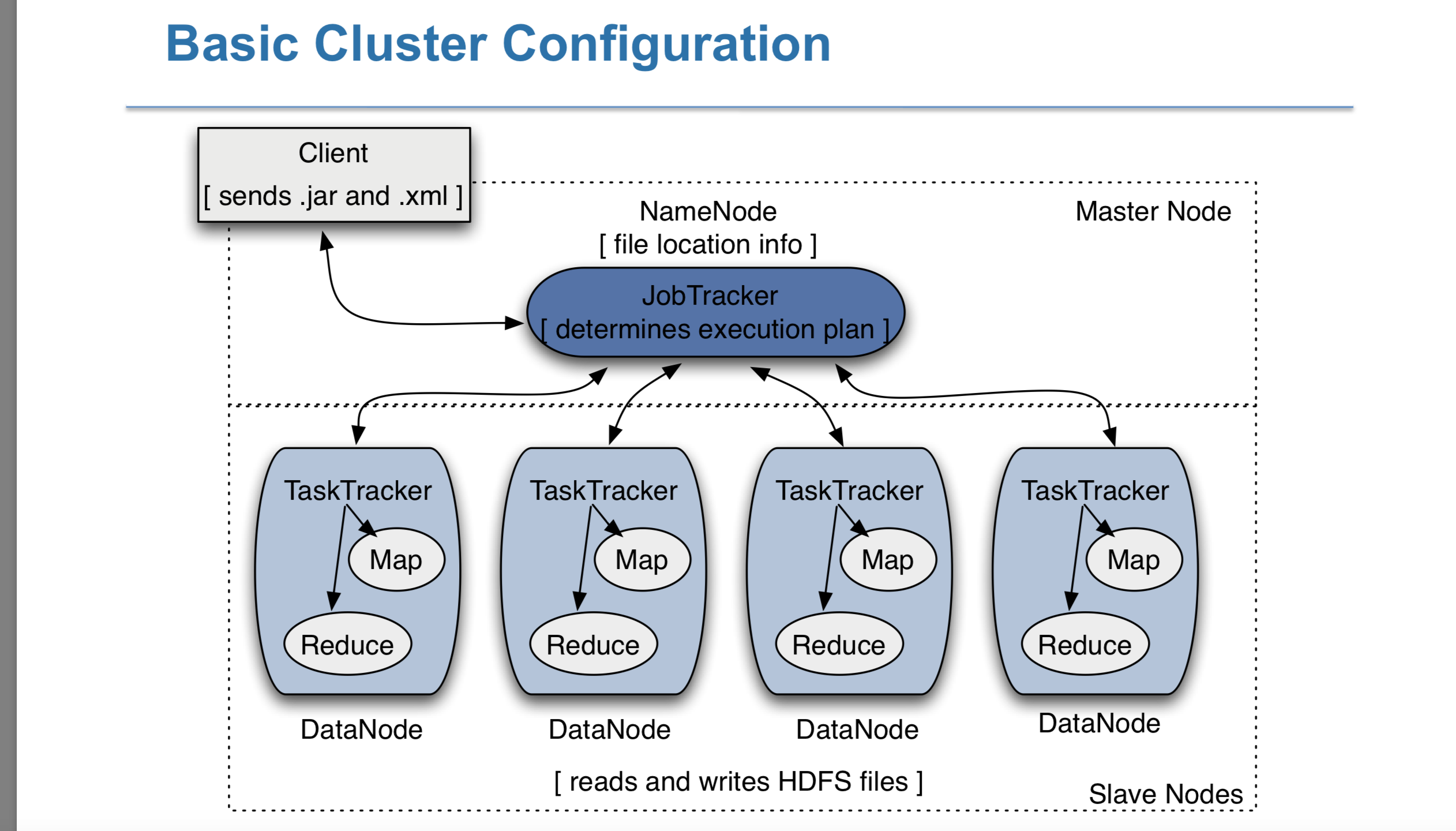
Hadoop consists of two core components
– The Hadoop Distributed File System (HDFS) : storing data on the cluster, split data into blocks and distributes across nodes and do replication
– MapReduce Software Framework : process data, After all Maps are complete, the MapReduce system distributes the intermediate data to nodes which perform the Reduce phase
A set of machines running HDFS and MapReduce is known as a Hadoop Cluster
(***) Files in HDFS are ‘write once’ –No random writes to files are allowed
HDFS is optimized for large, streaming reads of files –Rather than random reads
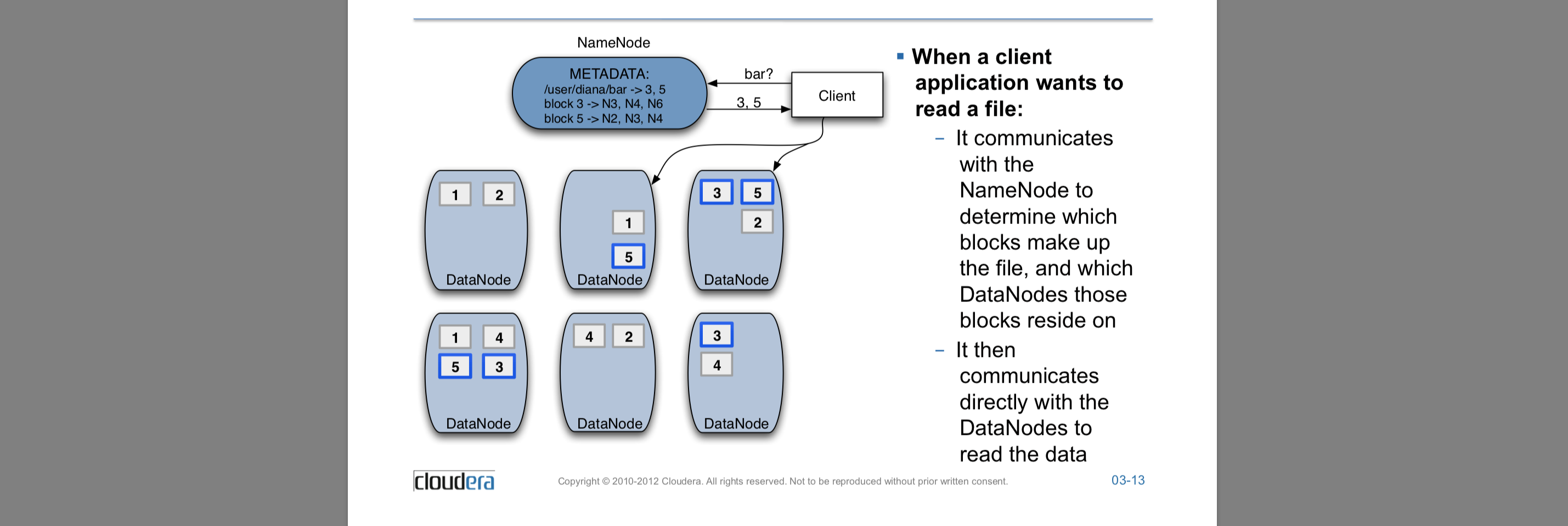
It has 2 components: Name node(master node)[file location info] and Data node(Slave node)[read and write HDFS files]. In Data node actual data is stored and name node stores the meta data that is the file location,
MapReduce is a method for distributing a task across multiple nodes. Mappers run on nodes which hold their portion of the data locally, to avoid network traffic.
(***)
The Mapper reads data in the form of key/value pairs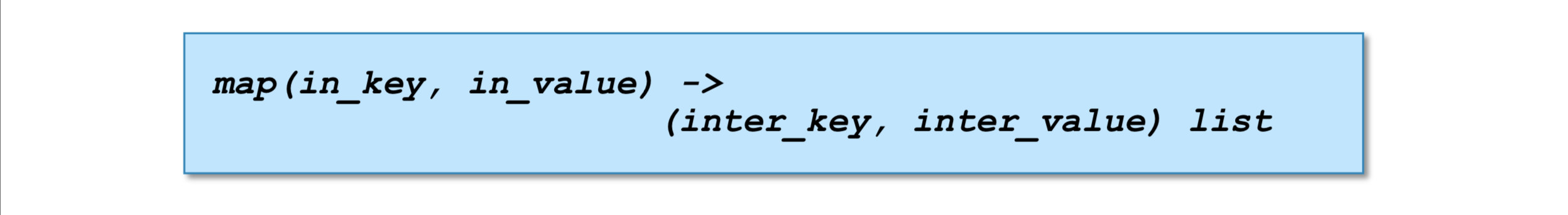 The Mapper may use or completely ignore the input key
The Mapper may use or completely ignore the input key
–The key is the byte offset into the file at which the line starts –The value is the contents of the line itself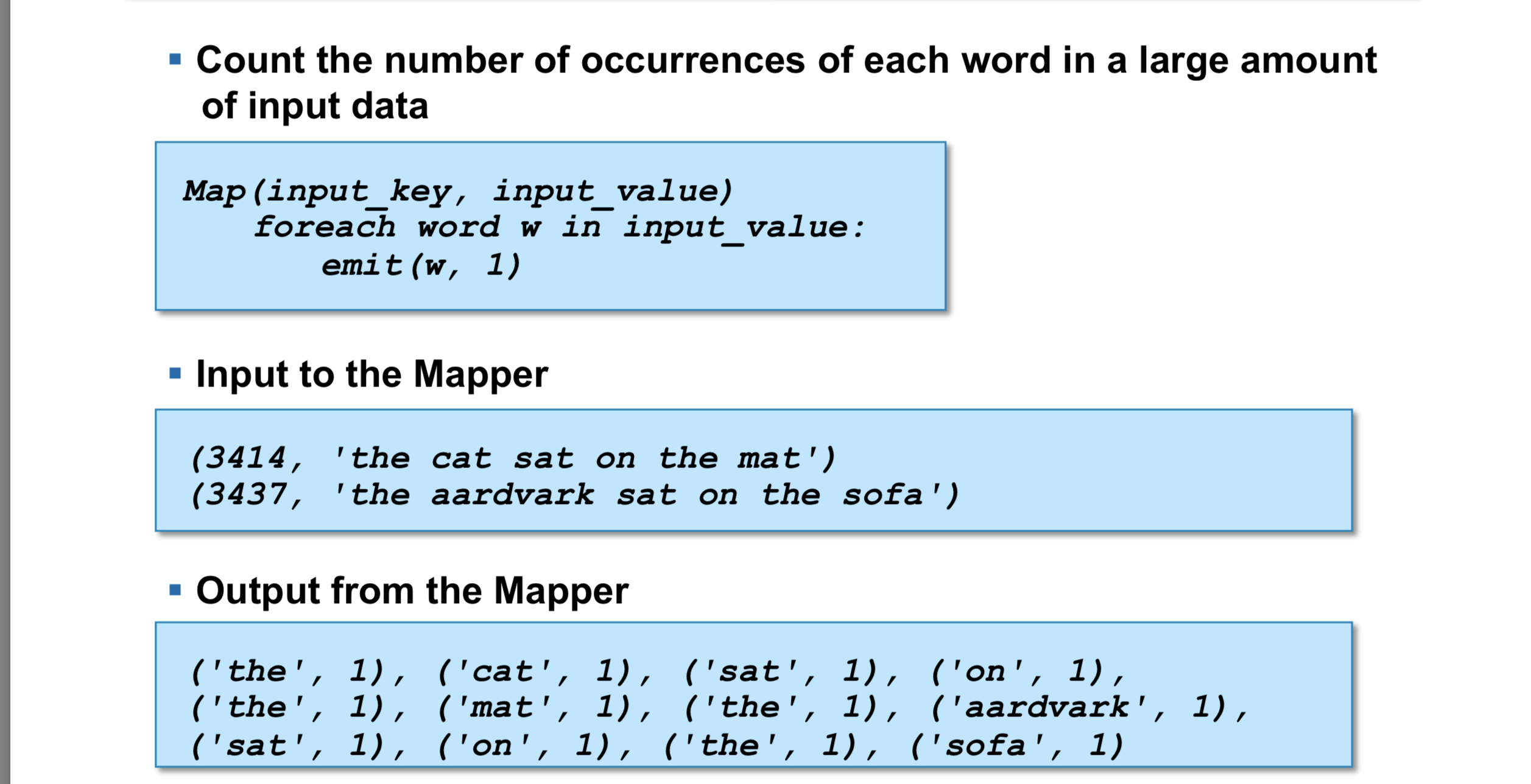 After the Map phase is over, all the intermediate values for a given intermediate key are combined together into a list
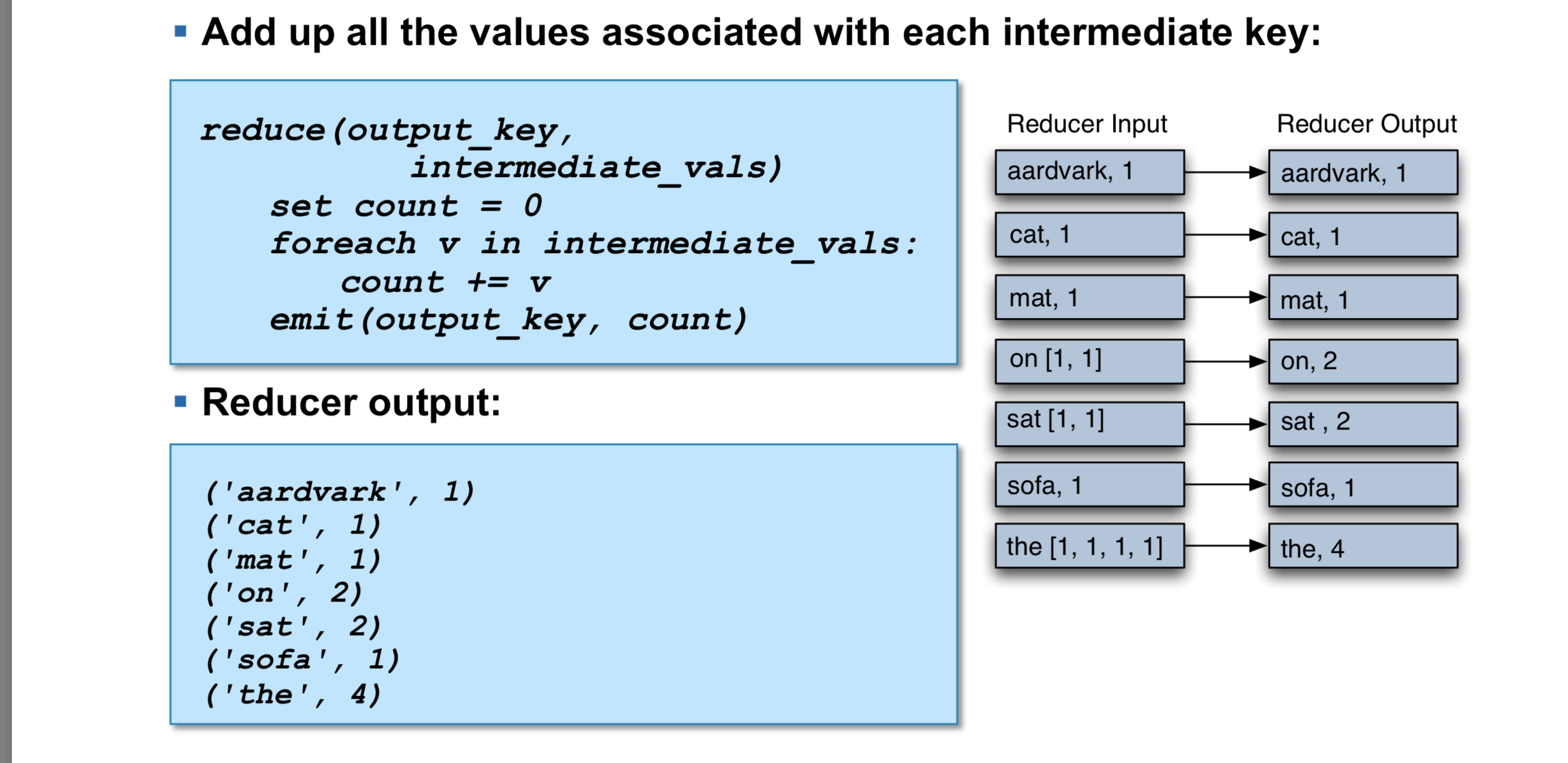
After the Map phase is over, all the intermediate values for a given intermediate key are combined together into a list
shuffle and sort:
shuffle -- All values associated with a particular intermediate key are guaranteed to go to the same Reducer
sort -- The intermediate keys, and their value lists, are passed to the Reducer in sorted key order
The Reducer outputs zero or more final key/value pairs, These are written to HDFS
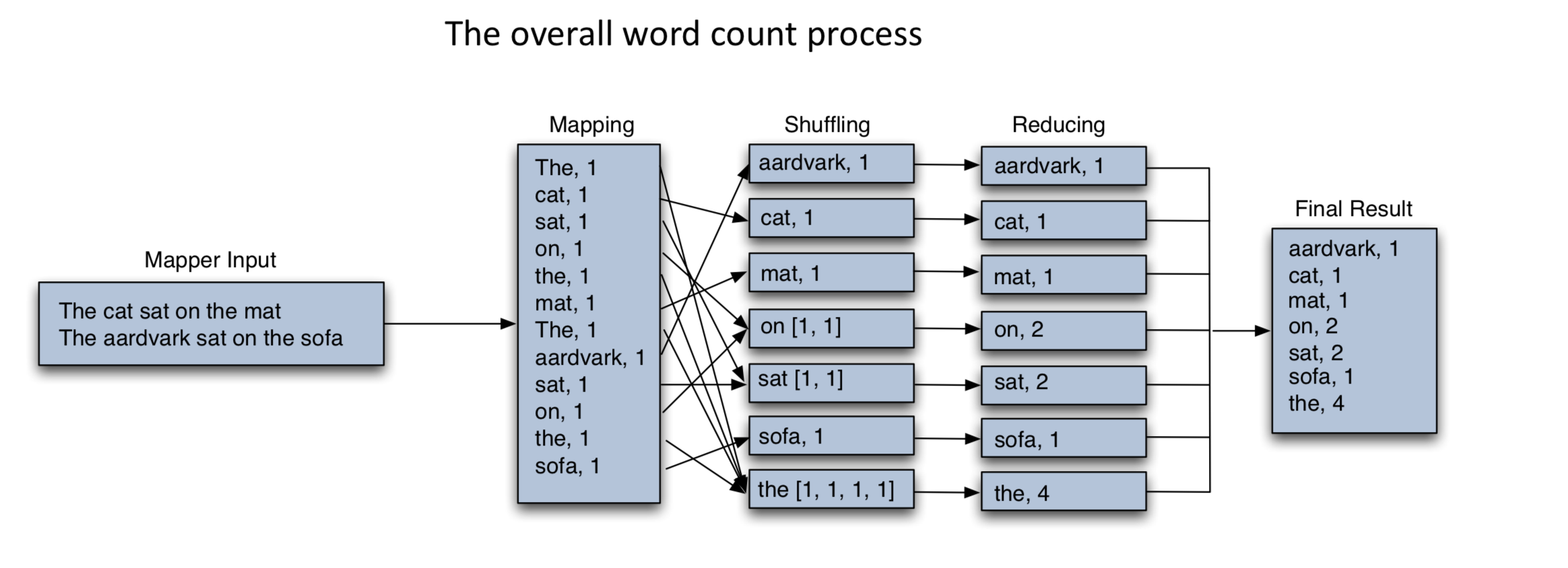
MapReduce breaks complex tasks down into smaller elements which can be executed in parallel
(***)
A typical PHP cURL usage follows the following sequence of steps.
curl_init – Initializes the session and returns a cURL handle which can be passed to other cURL functions.
- $ch = curl_init("www.google.com");
curl_setopt – This is the main work horse of cURL library. This function is called multiple times and specifies what we want the cURL library to do.
- curl_setopt($ch, CURLOPT_URL, "www.google.com");
- curl_setopt($ch, CURLOPT_FILE, $fp);
- curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
- curl_setopt($ch, CURLOPT_HEADER, 0);
curl_exec – Executes a cURL session.
- $contents = curl_exec ($ch);
- curl_exec($ch);
curl_close – Closes the current cURL session.
- curl_close($ch);
Security
- Spoofing – Fake the source of data
- Tampering – Change data in transit
- Snooping – Monitor sensitive data
- Replay – Intercept and resend data at a later time
The Goals of Security :
- Confidentiality – Assurance of data privacy
- Authentication – Assurance that an entity is who he/she/it claims to be
- Integrity – Assurance of non-alteration
- Availability – Assurance of data / services are available
Symmetric Key Encryption – Same key for encryption / decryption
Stream Ciphers – Takes the original data, divides it into digits, and encrypts each digit one at a time.
Block Ciphers – Divided up data into blocks of fixed length
- Electronic Codebook (ECB) : Plain text ➔ ECB block cipher encryption ➔ Cipher text
- Cipher Block Chaining (CBC) : Plain text ➔ XOR Previous Cipher ➔ ECB block cipher encryption ➔ Cipher text
- Cipher Feedback (CFB) : Previous Cipher text ➔ ECB block cipher encryption ➔ XOR Plain text -➔ Cipher text
- Output Feedback (OFB) : IV ➔ ECB block cipher encryption -➔ XOR Plain text ➔ Cipher text
- Counter (CTR) : counter ➔ ECB block cipher encryption ➔ XOR Plain text ➔ Cipher text
Message Digest
Fixed-size checksum created by cryptographic hash functions
- Preimage resistant : H = Hash (m), Given H cannot find m
- Second preimage resistant : Given m1, infeasible to find m2. Hash (m1) = Hash (m2)
- Collision-resistant : Infeasible to find m1 and m2 such that Hash (m1) = Hash (m2)
Message Authentication Code
Use secret key to address spoof data + hash problem
Public Key Cryptography
Each party has two keys: one is the private key where it must be kept secret, and one is the public key that can be freely distributed. One encrypts and the other one decrypts. PK is usually used as means for secret key exchange
Diffie-Hellman (DH)
Used for key agreement
Exchange of information over an insecure medium that allows each of two parties (sender and recipient) to compute a value that will be used to construct a secret key for a symmetric cipher during the rest of the communication.
RSA
RSA is the public key algorithm
Digital Signature
Use to ensure integrity, MAC is not useful due to the need of same secret key
PKI (Public Key infrastructure)
The goal of a certificate in PKI is to provide a mechanism that binds the public key to the claimed owner in a trustworthy manner.
A certificate authority (CA) that stores, issues and signs the digital certificates
A registration authority which verifies the identity of entities requesting their digital certificates to be stored at the CA
(***)Describe five step for X.509 public key certificate
- Generate private and public keys
- Gather name value pairs
- Generate Certificate Signing Request
- Submit Certificate Signing Request for CA to sign
- Receive certificate from CA
The public key is in a certificate signed by the CA. The public key is valid since I trust the CA.
(***)What does Trust mean?
“A” trusts “B” when “A” assumes that “B” will behave exactly as “A” expects
Web Trust Model
In a Web of Trust, everybody is a CA. Every user signs certificates for whoever he wants.
Advantages: Easy to implement, support Internet, it is there.
(***)Disadvantages:
- Identify Spoofing with “bad” CA cert
- Decentralized Trust Management – user level management
- Inability for Revocation
- Distribution Problem – Who get what version of browsers?
Reputation Trust Model
Centralized System
An authority is responsible for accumulating evaluations of agents from other agents. This authority then scores each agent with a reputation score. All reputations are public and global. Reputations of service providers are scored by consumers agents, and consumer agents’ reputations are scored by service providers agent.
Disadvantage:
- Artificial reputation score
- Agent Spoofing
- The revenge factor
<CANVAS>
The HTML<canvas>element is used to draw graphics, on the fly, via JavaScript.
The<canvas>element is only a container for graphics. You must use JavaScript to actually draw the graphics.
var c = document.getElementById("myCanvas");
var ctx = c.getContext("2d");
<VIDEO>
Thecontrolsattribute adds video controls, like play, pause, and volume.
It is a good idea to always includewidthandheightattributes. If height and width are not set, the page might flicker while the video loads.
The<source>element allows you to specify alternative video files which the browser may choose from. The browser will use the first recognized format.
The text between the<video>and</video>tags will only be displayed in browsers that do not support the<video>element.
<video width="320" height="240" autoplay>
<source src="movie.mp4" type="video/mp4">
<source src="movie.ogg" type="video/ogg">
Your browser does not support the video tag.
</video>
HTTP
(***)The "persistent HTTP" approach can re-use the same TCP connection for Multiple HTTP transfers, one after another, serially. Amortizes TCP overhead, but maintains TCP state longer at server.
The "pipelining" feature in HTTP/1.1 allows requests to be issued asynchronously on a persistent connection. Requests must be processed in proper order. Can do clever packaging.